一. OpenVPN 安装环境
Server 端的环境
Centos, kernel版本: 2.6.18-238.el5, IP 为 192.168.100.110
kernel 需要支持 tun 设备, 需要加载 iptables 模块.
检查 tun 是否安装:
代码:
view
plain
copy to clipboard
print
?
[root@sever160 ~]# modinfo tun [root@sever160 ~]# modinfo tun
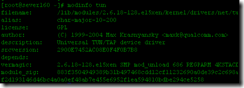
如果没有 modinfo 命令, 直接找一下, 看看 kernel 里是否有 tun.o
文件,但是本机的确是tun.ko,如果你找不到tun.o,那么你可以查找tun.ko:
代码:

检查iptables 模块, 查看是否有下列文件:
view
plain
copy to clipboard
print
?
# ls -l /etc/init.d/iptables
-rwxr-xr-x 1 root root 7135 2009-03-06 /etc/init.d/iptables # ls -l /etc/init.d/iptables
-rwxr-xr-x 1 root root 7135 2009-03-06 /etc/init.d/iptablesOpenVPN2.0.9下载地址:http://d3.yaoshi.com/yaoshidown/openvpn-2.0.9.tar.gz
更多版本:http://openvpn.net/release/
Client 端的环境:
openvpn-2.0_rc13-gui-1.0-rc3-install.exe Windows XP PRO SP2
openvpn-2.1.1-install.exe Windows 7
可在http://openvpn.net/release/ 下载
OpenVPN GUI的所有历史版本:
http://openvpn.se/files/install_packages/
二. OpenVPN 服务端安装过程
用 SecureCRT或者SSH登录到Linux服务器, 进入根目录
代码:
view
plain
copy to clipboard
print
?
#cd /usr/local/src/tarbag #cd /usr/local/src/tarbag 下载
LZO,解压到lzo-2.02.
下载 OpenVPN, 解压到openvpn-2.0.9
安装 LZO 代码:
view
plain
copy to clipboard
print
?
#tar -zxvf lzo-2.03.tar.gz -C ../software
#cd ../software/lzo-2.03
#./configure –prefix=/usr/local/lzo //设置安装路径
#make //编译
#make check //编译检查
#make install //安装 #tar -zxvf lzo-2.03.tar.gz -C ../software
#cd ../software/lzo-2.03
#./configure –prefix=/usr/local/lzo //设置安装路径
#make //编译
#make check //编译检查
#make install //安装
安装 OpenVPN
view
plain
copy to clipboard
print
?
#tar -xzvf openvpn-2.0.9.tar.gz -C ../software/
#cd /usr/local/src/software/openvpn-2.0.9
#./configure –prefix=/usr/local/openvpn –with-lzo-headers=/usr/local/lzo/include –with-lzo-lib=/usr/local/lzo/lib –with-ssl-headers=/usr/include/openssl –with-ssl-lib=/usr/lib
//以下为配置的输出内容
checking for ifconfig… /sbin/ifconfig
checking for ip… /sbin/ip
checking for route… /sbin/route
checking build system type… i686-pc-linux
checking host system type… i686-pc-linux
checking target system type… i686-pc-linux
checking for a BSD-compatible install… /usr/bin/install –c
………………
//检查LZO文件,如果这边没通过则无法安装OpenVPN
configure: checking for LZO Library and Header files…
checking lzo/lzo1x.h usability… yes
checking lzo/lzo1x.h presence… yes
checking for lzo/lzo1x.h… yes
checking for lzo1x_1_15_compress in -llzo2… yes
//检查SSL文件如果这边没通过则无法安装OpenVPN
configure: checking for OpenSSL Crypto Library and Header files…
checking openssl/evp.h usability… yes
checking openssl/evp.h presence… yes
checking for openssl/evp.h… yes
checking for EVP_CIPHER_CTX_init in -lcrypto… yes
//OpenSSL版本至少是0.9.6,如果不成功查查你的OpenSSL的版本
configure: checking that OpenSSL Library is at least version 0.9.6…
checking for EVP_CIPHER_CTX_set_key_length… yes
checking openssl/engine.h usability… yes
checking openssl/engine.h presence… yes
checking for openssl/engine.h… yes
checking for ENGINE_load_builtin_engines… yes
checking for ENGINE_register_all_complete… yes
checking for ENGINE_cleanup… yes
configure: checking for OpenSSL SSL Library and Header files…
checking openssl/ssl.h usability… yes
checking openssl/ssl.h presence… yes
checking for openssl/ssl.h… yes
checking for SSL_CTX_new in -lssl… yes
configure: creating ./config.status
config.status: creating Makefile
config.status: creating openvpn.spec
config.status: creating config-win32.h
config.status: creating install-win32/openvpn.nsi
config.status: creating config.h
config.status: executing depfiles commands
#make //编译,输出的内容就不粘贴了
#make install //最后一步,安装。 #tar -xzvf openvpn-2.0.9.tar.gz -C ../software/
#cd /usr/local/src/software/openvpn-2.0.9
#./configure –prefix=/usr/local/openvpn –with-lzo-headers=/usr/local/lzo/include –with-lzo-lib=/usr/local/lzo/lib –with-ssl-headers=/usr/include/openssl –with-ssl-lib=/usr/lib
//以下为配置的输出内容
checking for ifconfig… /sbin/ifconfig
checking for ip… /sbin/ip
checking for route… /sbin/route
checking build system type… i686-pc-linux
checking host system type… i686-pc-linux
checking target system type… i686-pc-linux
checking for a BSD-compatible install… /usr/bin/install –c
………………
//检查LZO文件,如果这边没通过则无法安装OpenVPN
configure: checking for LZO Library and Header files…
checking lzo/lzo1x.h usability… yes
checking lzo/lzo1x.h presence… yes
checking for lzo/lzo1x.h… yes
checking for lzo1x_1_15_compress in -llzo2… yes
//检查SSL文件如果这边没通过则无法安装OpenVPN
configure: checking for OpenSSL Crypto Library and Header files…
checking openssl/evp.h usability… yes
checking openssl/evp.h presence… yes
checking for openssl/evp.h… yes
checking for EVP_CIPHER_CTX_init in -lcrypto… yes
//OpenSSL版本至少是0.9.6,如果不成功查查你的OpenSSL的版本
configure: checking that OpenSSL Library is at least version 0.9.6…
checking for EVP_CIPHER_CTX_set_key_length… yes
checking openssl/engine.h usability… yes
checking openssl/engine.h presence… yes
checking for openssl/engine.h… yes
checking for ENGINE_load_builtin_engines… yes
checking for ENGINE_register_all_complete… yes
checking for ENGINE_cleanup… yes
configure: checking for OpenSSL SSL Library and Header files…
checking openssl/ssl.h usability… yes
checking openssl/ssl.h presence… yes
checking for openssl/ssl.h… yes
checking for SSL_CTX_new in -lssl… yes
configure: creating ./config.status
config.status: creating Makefile
config.status: creating openvpn.spec
config.status: creating config-win32.h
config.status: creating install-win32/openvpn.nsi
config.status: creating config.h
config.status: executing depfiles commands
#make //编译,输出的内容就不粘贴了
#make install //最后一步,安装。安装Pam插件.
首先检查pam-devel包是否安装
view
plain
copy to clipboard
print
?
# rpm -qa | grep pam
pam_smb-1.1.7-7.2.1
pam_pkcs11-0.5.3-23
pam-devel-0.99.6.2-6.el5_5.2
pam_krb5-2.2.14-18.el5
pam-0.99.6.2-6.el5_5.2
pam_krb5-2.2.14-18.el5
pam_pkcs11-0.5.3-23
pam-devel-0.99.6.2-6.el5_5.2
pam-0.99.6.2-6.el5_5.2
pam_ccreds-3-5
pam_smb-1.1.7-7.2.1
spamassassin-3.2.5-1.el5
pam_ccreds-3-5
pam_passwdqc-1.0.2-1.2.2
pam_passwdqc-1.0.2-1.2.2 # rpm -qa | grep pam
pam_smb-1.1.7-7.2.1
pam_pkcs11-0.5.3-23
pam-devel-0.99.6.2-6.el5_5.2
pam_krb5-2.2.14-18.el5
pam-0.99.6.2-6.el5_5.2
pam_krb5-2.2.14-18.el5
pam_pkcs11-0.5.3-23
pam-devel-0.99.6.2-6.el5_5.2
pam-0.99.6.2-6.el5_5.2
pam_ccreds-3-5
pam_smb-1.1.7-7.2.1
spamassassin-3.2.5-1.el5
pam_ccreds-3-5
pam_passwdqc-1.0.2-1.2.2
pam_passwdqc-1.0.2-1.2.2再检查mysql是否安装 (我的Mysql是编译安装的.所以不用rpm -qa检查.)
为了能使用OpenVPN的PAM验证插件,我们安装pam_mysql使用MySQL数据库存储用户数据,其它数据库可以找相应的PAM验证模块
view
plain
copy to clipboard
print
?
# tar zxvf pam_mysql-0.7RC1.tar.gz -C ../software/
#cd ../software/pam_mysql-0.7RC1/
#./configure –with-mysql=/usr/local/mysql/
#make
#make install # tar zxvf pam_mysql-0.7RC1.tar.gz -C ../software/
#cd ../software/pam_mysql-0.7RC1/
#./configure –with-mysql=/usr/local/mysql/
#make
#make install安装完成后会在/usr/lib/security/ 生成 pam_mysql.la pam_mysql.so
view
plain
copy to clipboard
print
?
#/usr/lib/security/
#ls
classpath.security pam_mysql.la pam_mysql.so #/usr/lib/security/
#ls
classpath.security pam_mysql.la pam_mysql.so接下来生成openvpn插件openvpn-auth-pam.so
到Openvpn源码目录
view
plain
copy to clipboard
print
?
#cd /usr/local/src/software/openvpn-2.0.9/plugin/auth-pam/
#make #cd /usr/local/src/software/openvpn-2.0.9/plugin/auth-pam/
#make在目录下会生成openvpn-auth-pam.so
将文件抟到openvpn目录下方便使用
view
plain
copy to clipboard
print
?
#cp openvpn-auth-pam.so /usr/local/openvpn/ #cp openvpn-auth-pam.so /usr/local/openvpn/配置数据库
以管理员身份登录数据库:
view
plain
copy to clipboard
print
?
mysql> create database vpn;
mysql> GRANT ALL ON vpn.* TO vpn@localhost IDENTIFIED BY 'vpn123';
mysql> flush privileges;
mysql> use vpn;
mysql> Create TABLE vpnuser (
-> name char(20) NOT NULL,
-> password char(128) default NULL,
-> active int(10) NOT NULL DEFAULT 1,
-> PRIMARY KEY (name)
-> );
mysql> insert into vpnuser (name,password) values('hsf',password('hsf')); mysql> create database vpn;
mysql> GRANT ALL ON vpn.* TO vpn@localhost IDENTIFIED BY 'vpn123';
mysql> flush privileges;
mysql> use vpn;
mysql> Create TABLE vpnuser (
-> name char(20) NOT NULL,
-> password char(128) default NULL,
-> active int(10) NOT NULL DEFAULT 1,
-> PRIMARY KEY (name)
-> );
mysql> insert into vpnuser (name,password) values('hsf',password('hsf')); #创建vpn用户,对vpn这个database有所有操作权限,密码为vpn123
#active不为1,无权使用VPN
#增加用户 用户名:hsf密码:hsf 这个用户为vpn用户.测试用.
配置pam_mysql模块
创建/etc/pam.d/openvpn文件,文件内容如下:
view
plain
copy to clipboard
print
?
auth sufficient /usr/lib/security/pam_mysql.so user=vpn passwd=vpn123 host=localhost db=vpn table=vpnuser usercolumn=name passwdcolumn=password where=active=1 sqllog=0 crypt=2
account required /usr/lib/security/pam_mysql.so user=vpn passwd=vpn123 host=localhost db=vpn table=vpnuser usercolumn=name passwdcolumn=password where=active=1 sqllog=0 crypt=2 auth sufficient /usr/lib/security/pam_mysql.so user=vpn passwd=vpn123 host=localhost db=vpn table=vpnuser usercolumn=name passwdcolumn=password where=active=1 sqllog=0 crypt=2
account required /usr/lib/security/pam_mysql.so user=vpn passwd=vpn123 host=localhost db=vpn table=vpnuser usercolumn=name passwdcolumn=password where=active=1 sqllog=0 crypt=2注释:
crypt(0) — Used to decide to use MySQL's PASSWORD() function or crypt()
0 = No encryption. Passwords in database in plaintext. NOT recommended!
1 = Use crypt
2 = Use MySQL PASSWORD() function
下面可以测试pam_mysql是否工作正常,先检查saslauthd是否安装:
view
plain
copy to clipboard
print
?
# rpm -qa | grep sasl
cyrus-sasl-lib-2.1.22-5.el5_4.3
cyrus-sasl-plain-2.1.22-5.el5_4.3
cyrus-sasl-lib-2.1.22-5.el5_4.3
cyrus-sasl-2.1.22-5.el5_4.3
cyrus-sasl-devel-2.1.22-5.el5_4.3
cyrus-sasl-md5-2.1.22-5.el5_4.3
cyrus-sasl-plain-2.1.22-5.el5_4.3
cyrus-sasl-2.1.22-5.el5_4.3
cyrus-sasl-devel-2.1.22-5.el5_4. # rpm -qa | grep sasl
cyrus-sasl-lib-2.1.22-5.el5_4.3
cyrus-sasl-plain-2.1.22-5.el5_4.3
cyrus-sasl-lib-2.1.22-5.el5_4.3
cyrus-sasl-2.1.22-5.el5_4.3
cyrus-sasl-devel-2.1.22-5.el5_4.3
cyrus-sasl-md5-2.1.22-5.el5_4.3
cyrus-sasl-plain-2.1.22-5.el5_4.3
cyrus-sasl-2.1.22-5.el5_4.3
cyrus-sasl-devel-2.1.22-5.el5_4. 有cyrus-sasl-2.1.22-5.el5_4.3应该就可以了,如果没有请安装相应的软件包,不安装也行,可以通过其它方法测试
view
plain
copy to clipboard
print
?
[root@vpn ~]# saslauthd -a pam
[root@vpn ~]# testsaslauthd -u elm -p elm -s openvpn
0: OK "Success." [root@vpn ~]# saslauthd -a pam
[root@vpn ~]# testsaslauthd -u elm -p elm -s openvpn
0: OK "Success." 我前面出现一个错误
0: "authentication fail." 是因为pam_mysql.so路径指定错误,没有找到这个模块去认证.
下面可以开始配置OpenVPN服务器了
view
plain
copy to clipboard
print
?
#cp -r /usr/local/src/software/openvpn-2.0.9/easy-rsa /usr/local/openvpn
生成证书Key
初始化 PKI
代码:
#cd /usr/local/openvpn/easy-rsa/2.0
#vi vars
修改以下内容
————-开始——————
export EASY_RSA="`pwd`"
export KEY_CONFIG=`$EASY_RSA/whichopensslcnf $EASY_RSA`
export KEY_CONFIG=$EASY_RSA/openssl.cnf
export KEY_DIR=$EASY_RSA/keys
export KEY_SIZE=1024
export KEY_COUNTRY=CN
export KEY_PROVINCE=BJ
export KEY_CITY=BJ
export KEY_ORG="netgaming"
export KEY_EMAIL="support@yaoshi.com"
———–结束——————-
Build:
#source ./vars
#./clean-all //删除keys文件夹
#./build-ca //建立根证书
[root@sever160 2.0]# ./build-ca
Generating a 1024 bit RSA private key
..++++++
…………………………………….++++++
writing new private key to 'ca.key'
—–
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
—–
Country Name (2 letter code) [CN]:CN
State or Province Name (full name) [BJ]:BJ
Locality Name (eg, city) [BJ]:BJ
organization Name (eg, company) [netgaming]:netgaming
organizational Unit Name (eg, section) []:yaoshi
Common Name (eg, your name or your server's hostname) [netgaming CA]:server
Email Address [support@yaoshi.com]:support@yaoshi.com
# 建立 server key 代码:
代码:
#./build-key-server server
[root@sever160 2.0]# ./build-key-server server
Generating a 1024 bit RSA private key
………………..++++++
………………………..++++++
writing new private key to 'server.key'
—–
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
—–
Country Name (2 letter code) [CN]:CN
State or Province Name (full name) [BJ]:BJ
Locality Name (eg, city) [BJ]:BJ
organization Name (eg, company) [netgaming]:netgaming
organizational Unit Name (eg, section) []:yaoshi
Common Name (eg, your name or your server's hostname) [server]:server
Email Address [support@yaoshi.com]:support@yaoshi.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:yaoshi
An optional company name []:yaoshi
Using configuration from /usr/local/openvpn/easy-rsa/2.0/openssl.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'BJ'
localityName :PRINTABLE:'BJ'
organizationName :PRINTABLE:'netgaming'
organizationalUnitName:PRINTABLE:'yaoshi'
commonName :PRINTABLE:'server'
emailAddress :IA5STRING:'support@yaoshi.com'
Certificate is to be certified until Sep 1 06:11:47 2019 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@sever160 2.0]# ./build-dh
Generating DH parameters, 1024 bit long safe prime, generator 2
This is going to take a long time
…+…………………………………….+…..+……+.+………………..+……………………………………………………………+…………………..+…………….+..+………………+.+…………………………………………………….+.+…………..+………………………………………………..+…+…………………………………..+……………..++*++*++* #cp -r /usr/local/src/software/openvpn-2.0.9/easy-rsa /usr/local/openvpn
生成证书Key
初始化 PKI
代码:
#cd /usr/local/openvpn/easy-rsa/2.0
#vi vars
修改以下内容
————-开始——————
export EASY_RSA="`pwd`"
export KEY_CONFIG=`$EASY_RSA/whichopensslcnf $EASY_RSA`
export KEY_CONFIG=$EASY_RSA/openssl.cnf
export KEY_DIR=$EASY_RSA/keys
export KEY_SIZE=1024
export KEY_COUNTRY=CN
export KEY_PROVINCE=BJ
export KEY_CITY=BJ
export KEY_ORG="netgaming"
export KEY_EMAIL="support@yaoshi.com"
———–结束——————-
Build:
#source ./vars
#./clean-all //删除keys文件夹
#./build-ca //建立根证书
[root@sever160 2.0]# ./build-ca
Generating a 1024 bit RSA private key
..++++++
…………………………………….++++++
writing new private key to 'ca.key'
—–
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
—–
Country Name (2 letter code) [CN]:CN
State or Province Name (full name) [BJ]:BJ
Locality Name (eg, city) [BJ]:BJ
organization Name (eg, company) [netgaming]:netgaming
organizational Unit Name (eg, section) []:yaoshi
Common Name (eg, your name or your server's hostname) [netgaming CA]:server
Email Address [support@yaoshi.com]:support@yaoshi.com
# 建立 server key 代码:
代码:
#./build-key-server server
[root@sever160 2.0]# ./build-key-server server
Generating a 1024 bit RSA private key
………………..++++++
………………………..++++++
writing new private key to 'server.key'
—–
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
—–
Country Name (2 letter code) [CN]:CN
State or Province Name (full name) [BJ]:BJ
Locality Name (eg, city) [BJ]:BJ
organization Name (eg, company) [netgaming]:netgaming
organizational Unit Name (eg, section) []:yaoshi
Common Name (eg, your name or your server's hostname) [server]:server
Email Address [support@yaoshi.com]:support@yaoshi.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:yaoshi
An optional company name []:yaoshi
Using configuration from /usr/local/openvpn/easy-rsa/2.0/openssl.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'BJ'
localityName :PRINTABLE:'BJ'
organizationName :PRINTABLE:'netgaming'
organizationalUnitName:PRINTABLE:'yaoshi'
commonName :PRINTABLE:'server'
emailAddress :IA5STRING:'support@yaoshi.com'
Certificate is to be certified until Sep 1 06:11:47 2019 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@sever160 2.0]# ./build-dh
Generating DH parameters, 1024 bit long safe prime, generator 2
This is going to take a long time
…+…………………………………….+…..+……+.+………………..+……………………………………………………………+…………………..+…………….+..+………………+.+…………………………………………………….+.+…………..+………………………………………………..+…+…………………………………..+……………..++*++*++*
创建服务端配置文件
view
plain
copy to clipboard
print
?
#mkdir /usr/local/openvpn/etc //新建openvpn配置文件存放目录
#vi /usr/local/openvpn/etc/server.conf
local 192.168.100.110
port 1194
proto udp
dev tun
ca /usr/local/openvpn/easy-rsa/2.0/keys/ca.crt
cert /usr/local/openvpn/easy-rsa/2.0/keys/server.crt
key /usr/local/openvpn/easy-rsa/2.0/keys/server.key # This file should be kept secret
dh /usr/local/openvpn/easy-rsa/2.0/keys/dh1024.pem
server 10.8.0.0 255.255.255.0
client-to-client
plugin /usr/local/openvpn/openvpn-auth-pam.so openvpn
client-cert-not-required
username-as-common-name
user nobody
group nobody
keepalive 10 120
comp-lzo
persist-key
persist-tun
ifconfig-pool-persist /usr/local/openvpn/log/openvpn/ipp.txt
status /usr/local/openvpn/log/openvpn-status.log
log /usr/local/openvpn/log/openvpn.log
log-append /usr/local/openvpn/log/openvpn.log
verb 4
push "dhcp-option DNS 192.168.100.210"
push "route 10.8.0.0 255.255.255.0" #mkdir /usr/local/openvpn/etc //新建openvpn配置文件存放目录
#vi /usr/local/openvpn/etc/server.conf
local 192.168.100.110
port 1194
proto udp
dev tun
ca /usr/local/openvpn/easy-rsa/2.0/keys/ca.crt
cert /usr/local/openvpn/easy-rsa/2.0/keys/server.crt
key /usr/local/openvpn/easy-rsa/2.0/keys/server.key # This file should be kept secret
dh /usr/local/openvpn/easy-rsa/2.0/keys/dh1024.pem
server 10.8.0.0 255.255.255.0
client-to-client
plugin /usr/local/openvpn/openvpn-auth-pam.so openvpn
client-cert-not-required
username-as-common-name
user nobody
group nobody
keepalive 10 120
comp-lzo
persist-key
persist-tun
ifconfig-pool-persist /usr/local/openvpn/log/openvpn/ipp.txt
status /usr/local/openvpn/log/openvpn-status.log
log /usr/local/openvpn/log/openvpn.log
log-append /usr/local/openvpn/log/openvpn.log
verb 4
push "dhcp-option DNS 192.168.100.210"
push "route 10.8.0.0 255.255.255.0"注释:
client-to-client
#如果让Client之间可以相互看见,去掉本行的注释掉,否则Client之间无法相互访问
duplicate-cn
#是否允许一个User同时登录多次,去掉本行注释后可以使用同一个用户名登录多次
plugin
/usr/local/openvpn/openvpn-auth-pam.so openvpn
#说明使用的插件,openvpn为插件的参数,使用pam的servicesname
client-cert-not-required
#不请求客户的CA证书,使用User/Pass验证
username-as-common-name #使用客户提供的UserName作为Common
Name
#接下来配置客户端的配置文件client.ovpn(拿给windows客户端使用的):
view
plain
copy to clipboard
print
?
client
dev tun
proto udp
remote VPN_IP或者域名 1194
persist-key
persist-tun
ca ca.crt
auth-user-pass
ns-cert-type server
comp-lzo
verb 3
redirect-gateway def1 client
dev tun
proto udp
remote VPN_IP或者域名 1194
persist-key
persist-tun
ca ca.crt
auth-user-pass
ns-cert-type server
comp-lzo
verb 3
redirect-gateway def1 注释:
auth-user-pass #询问用户名和密码
启动Openvpn:
view
plain
copy to clipboard
print
?
#cd /usr/local/openvpn/sbin/
#./openvpn –daemon –config /usr/local/openvpn/etc/server.conf #cd /usr/local/openvpn/sbin/
#./openvpn –daemon –config /usr/local/openvpn/etc/server.conf
三. OpenVPN For Windows 客户端安装过程 (把客户端装在U盘里看第九点)
安装 OpenVPN For Windows, 到
http://openvpn.se
下载. 目前的版本是 1.0.3. 注意: OpenVPN 的版本要和 OpenVPN Server 的版本配套.
配置 openvpn gui
安装结束后, 进入安装文件夹下的 config 目录, 然后将 client.ovpn 文件从 server 上下载到此文件夹
同时, ca.crt下载到此文件夹中.
然后双击 client.ovpn 即可启动 openvpn, 或者通过 OpenVPN GUI 的控制启动 VPN.
如果双击 client.ovpn 没有反应, 则在任务栏点 OpenVPN GUI 的小图标右键, 选择 edit config, 将内容复制过去再保存.
然后再点右键中的 connect即可.
五. OpenVPN 访问外网的设置
打开路由 VPN连接成功后, 还需要设置路由, 才能透过VPN访问Internet. 在 linux服务器上添加路由:
(备注:如果openvpn服务器不是直接接外网,只是接在局域网交换机上的一台普通线路上,则需要在路由器上添加一条到192.168.100.110的1194端口映射)
代码:
#iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j SNAT –to-source
192.168.100.110 (出口IP地址,和server.conf中local
192.168.100.110这个IP相同)
#/etc/init.d/iptables save
#/etc/init.d/iptables
restart
不同的机器,-o eth0 参数可能不一样,具体可输入 ifconfig 查看,搞清 ip(192.168.100.110)所在的网卡号.
同时, 需要将 ip forward 打开. 不要用 echo 1 > /proc/sys/net/ipv4/ip_forward 的方式,
这种方式重启后无效. 先查看一下:
代码:
view
plain
copy to clipboard
print
?
#sysctl -a | grep for
#查看结果:
net.ipv4.conf.tun0.force_igmp_version = 0
net.ipv4.conf.tun0.mc_forwarding = 0
net.ipv4.conf.tun0.forwarding = 1
net.ipv4.conf.eth0.force_igmp_version = 0
net.ipv4.conf.eth0.mc_forwarding = 0
net.ipv4.conf.eth0.forwarding = 1
net.ipv4.conf.lo.force_igmp_version = 0
net.ipv4.conf.lo.mc_forwarding = 0
net.ipv4.conf.lo.forwarding = 1
net.ipv4.conf.default.force_igmp_version = 0
net.ipv4.conf.default.mc_forwarding = 0
net.ipv4.conf.default.forwarding = 1
net.ipv4.conf.all.force_igmp_version = 0
net.ipv4.conf.all.mc_forwarding = 0
net.ipv4.conf.all.forwarding = 1
net.ipv4.ip_forward = 1 #sysctl -a | grep for
#查看结果:
net.ipv4.conf.tun0.force_igmp_version = 0
net.ipv4.conf.tun0.mc_forwarding = 0
net.ipv4.conf.tun0.forwarding = 1
net.ipv4.conf.eth0.force_igmp_version = 0
net.ipv4.conf.eth0.mc_forwarding = 0
net.ipv4.conf.eth0.forwarding = 1
net.ipv4.conf.lo.force_igmp_version = 0
net.ipv4.conf.lo.mc_forwarding = 0
net.ipv4.conf.lo.forwarding = 1
net.ipv4.conf.default.force_igmp_version = 0
net.ipv4.conf.default.mc_forwarding = 0
net.ipv4.conf.default.forwarding = 1
net.ipv4.conf.all.force_igmp_version = 0
net.ipv4.conf.all.mc_forwarding = 0
net.ipv4.conf.all.forwarding = 1
net.ipv4.ip_forward = 1
如果你的主机上列数值(*.forwarding)不是为1, 则要将其改成1。
代码:
view
plain
copy to clipboard
print
?
#sysctl -w net.ipv4.conf.eth0.forwarding = 1 #sysctl -w net.ipv4.conf.eth0.forwarding = 1 (系统重启后所有forwarding又重置为0,所以把这些命令加入rc.local中或者修改/etc/sysctl.conf)
//以下内容yaoshi可选
———–开始————–
开启域名服务器
如果你需要访问一些已经被GFW封掉了域名的网站, 但你的 OpenVPN 服务器没有被封的话,那么你需要在你的主机上开启 name server, 并将
dns push 给 client。 一般的独立主机, 都带有 private dns server.
代码:
view
plain
copy to clipboard
print
?
rpm -qa | grep bind
/etc/init.d/named start rpm -qa | grep bind
/etc/init.d/named start 另外, 必须保证 server.conf 配置中, 有这三个配置:
代码:
view
plain
copy to clipboard
print
?
push "dhcp-option DNS 10.8.0.1"
push "dhcp-option DNS 192.168.100.210" # name server 地址 push "dhcp-option DNS 10.8.0.1"
push "dhcp-option DNS 192.168.100.210" # name server 地址 ——–结束————-
当 client 连接成功后, 在 cmd 下执行 ipconfig /all, 应该有这类似这样的输出:
代码:
Ethernet adapter 本地连接 4:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : TAP-Win32 Adapter V8
Physical Address. . . . . . . . . : 00-FF-2B-EA-C0-89
Dhcp Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IP Address. . . . . . . . . . . . : 10.8.0.26
Subnet Mask . . . . . . . . . . . : 255.255.255.252
Default Gateway . . . . . . . . . : 10.8.0.25
DHCP Server . . . . . . . . . . . : 10.8.0.25
DNS Servers . . . . . . . . . . . : 218.85.157.99
218.85.152.99
Lease Obtained. . . . . . . . . . : 2009年9月4日星期五 9:15:42
Lease Expires . . . . . . . . . . : 2010年9月4日星期六 9:15:42
六. 设置 OpenVPN 服务器 reboot后自动启动 openvpn
执行命令:
代码:
vi /etc/rc.local 然后在最后面加入此行:
代码:
view
plain
copy to clipboard
print
?
#/usr/local/openvpn/sbin/openvpn –daemon –config /usr/local/openvpn/etc/server.conf > /dev/null 2>&1 & #/usr/local/openvpn/sbin/openvpn –daemon –config /usr/local/openvpn/etc/server.conf > /dev/null 2>&1 &
七. OpenVPN 测试
1、你可以用 VPN 登录上去之后, 测试 MSN, QQ, IE 等网络应用, 也可以尝试访问一些被 GFW 禁掉的网站, 当然, 前提是你的 VPN
服务器不在境内.
2、不连接VPN,打开
www.ip138.com查看本机IP外网ip
地址,然后连接VPN再打开一次,对比两次的IP地址。
七、常见问题:
1、 客户端本地连接没有网关
检查client.ovpn配置文件中是否有redirect-gateway def1
2、 可以拨内网的IP地址192.168.100.110,无法拨通218.66.36.119
检查客户端是否被限制访问外部网络
3、 提示证书无效
检查openvpn服务器的时间是否正确,如果不正确,请在修改时间后重新制作证书
4、 如何检查所有网络是否走VPN线路
Windows下使用命令tracert 218.85.157.99或者pathping 218.85.157.99
例如:
C:/>tracert 218.85.157.99
Tracing route to BJ-DNS.BJ.BJ.cn [218.85.157.99]
over a maximum of 30 hops:
1 1 ms
(第一跳是VPN服务器网关,如果不是这个说明失败)
2 1 ms 1 ms 1 ms 192.168.50.254(VPN所在网络网关)
3 2 ms 2 ms 2 ms 218.66.36.254
4 4 ms 1 ms 1 ms 220.160.92.105
5 2 ms 2 ms 2 ms 202.109.204.161
6 2 ms 1 ms 2 ms 218.85.156.90
7 * * * Request timed out.
8 3 ms 3 ms 4 ms BJ-DNS.BJ.BJ.cn [218.85.157.99]
Trace complete.
Linux下使用命令tracert 218.85.157.99或者tracertpaht 218.85.157.99
5、 为什么我在不同的电脑上拨VPN客户端得ip地址都是一样的呢?
检查你是否使用了同一个客户端证书
6、 为什么一台电脑拨号可以正常使用,当两台同时拨号就不行呢?
检查你是否使用了同一个客户端证书。
7、 断开VPN马上连接发现连接不上?
连接还未释放所以连不上,你修改本机的ip地址就能重新连接VPN了。
8、 OPENVPN有段时间没有使用,今天重新建证书,一切完毕之后发现连接上了却无法上网
现在的IP地址从100修改为111,NAT没有重新设置,于是打开/etc/sysconfig/iptables把NAT转发规则从:
-A POSTROUTING -s 10.8.0.0/255.255.255.0 -o eth0 -j SNAT –to-source
192.168.100.110
改为:
-A POSTROUTING -s 10.8.0.0/255.255.255.0 -o eth0 -j SNAT –to-source
192.168.100.111
搞定~~~~~
八. 添加用户
view
plain
copy to clipboard
print
?
mysql> use vpn;
Database changed
mysql> insert into vpnuser (name,password) values('用户',password('密码')); mysql> use vpn;
Database changed
mysql> insert into vpnuser (name,password) values('用户',password('密码'));
九. 其他安全配置(将客户端安装在U盘内.)
USERNAME/PASSWORD验证方式比证书方式更安全而且更方便.
因为客户端只需要一个ca.crt与client.ovpn两个配置文件. 不需要生成证书. 即使被外人得到了ca文件也还需要帐号密码才能连上vpn.
如果再将客户端安装到U盘里将配置文件都隐藏起来.像银行的U盾一样. 插上U盘才能连接VPN. 大大的提高了安全性.
下面说下简单的做法.已经实现:
首先说下制作iso. 使用UltraISO工具 .
下载一个叫Netvpn的绿色版本vpn 这个版本的vpn全自动识别windows的版本.安装相应的虚拟网卡.
在制作iso的时候将其他配置文件都设成隐藏文件.这样就无法看到这些文件了.
然后关于U盘,我们需要将U盘改成usb-cdrom模式.这样的好处是可以将U盘当光盘来使用.只读.并且可以隐藏配置文件,即使U盘遗失了,也不会丢失ca文件.
将U盘改成usb-cdrom模式需要用到量产工具.其中相关知识自己百度去哈.
我这里使用的是金士顿dt100 g2 4g U盘. U盘信息检测工具检测错了我的主控.导致我用错了量产工具,使这个U盘报废了.
这个U盘的主控应该是群联 Ps2251-50
量产U盘最关键的就是找对主控,跟匹配的工具.
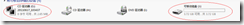
其中G盘就是我的U盘改成的CD-ROM.2.56M J盘是U盘剩下的空间 3.72G.可以像普通U盘一样使用.
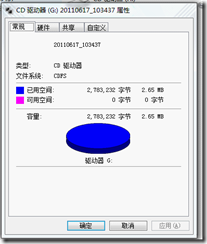
看下里面的内容:
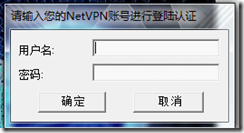
只要打开openvpn.exe 输入用户密码就能连接vpn了.
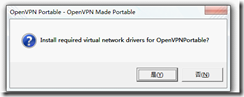
打开openvpn.exe会先提示你安装虚拟网卡:
启动画面

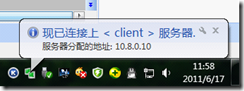
当你退出vpn时会提示你卸载虚拟网卡.
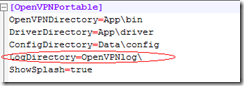
Ps:这里有一个不完美的地方. 就是这个绿色版客户端需要写日志. 我们把U盘改成了CD-ROM就不能写入日志.会报一个日志不能写入的错误.
这个日志无法指定到其他盘符.只能限制在这个目录里面.有点类似与chroot. 我弄了一个D盘的快捷方式也不会写到这个快捷方式里.
在本地测试的时候.它会新建一个目录.而不会写到快捷方式的那个目录里.
没有其他办法了.先这样用了. 下面是这个客户端的关于日志的配置.如果谁有其他办法可以告之我下.
来源:http://blog.csdn.net/deccmtd/article/details/6551151
 席天卷地个人博客
席天卷地个人博客


评论前必须登录!
注册